Kenna Leaked 2026 Folder HQ Vids/Pics Direct Link
Launch Now kenna leaked top-tier digital broadcasting. No subscription costs on our content platform. Plunge into in a vast collection of media made available in 4K resolution, optimal for passionate streaming geeks. With hot new media, you’ll always receive updates. Browse kenna leaked tailored streaming in breathtaking quality for a totally unforgettable journey. Hop on board our video library today to enjoy one-of-a-kind elite content with zero payment required, no need to subscribe. Stay tuned for new releases and uncover a galaxy of unique creator content produced for first-class media buffs. Make sure you see singular films—download quickly! See the very best from kenna leaked exclusive user-generated videos with vivid imagery and hand-picked favorites.
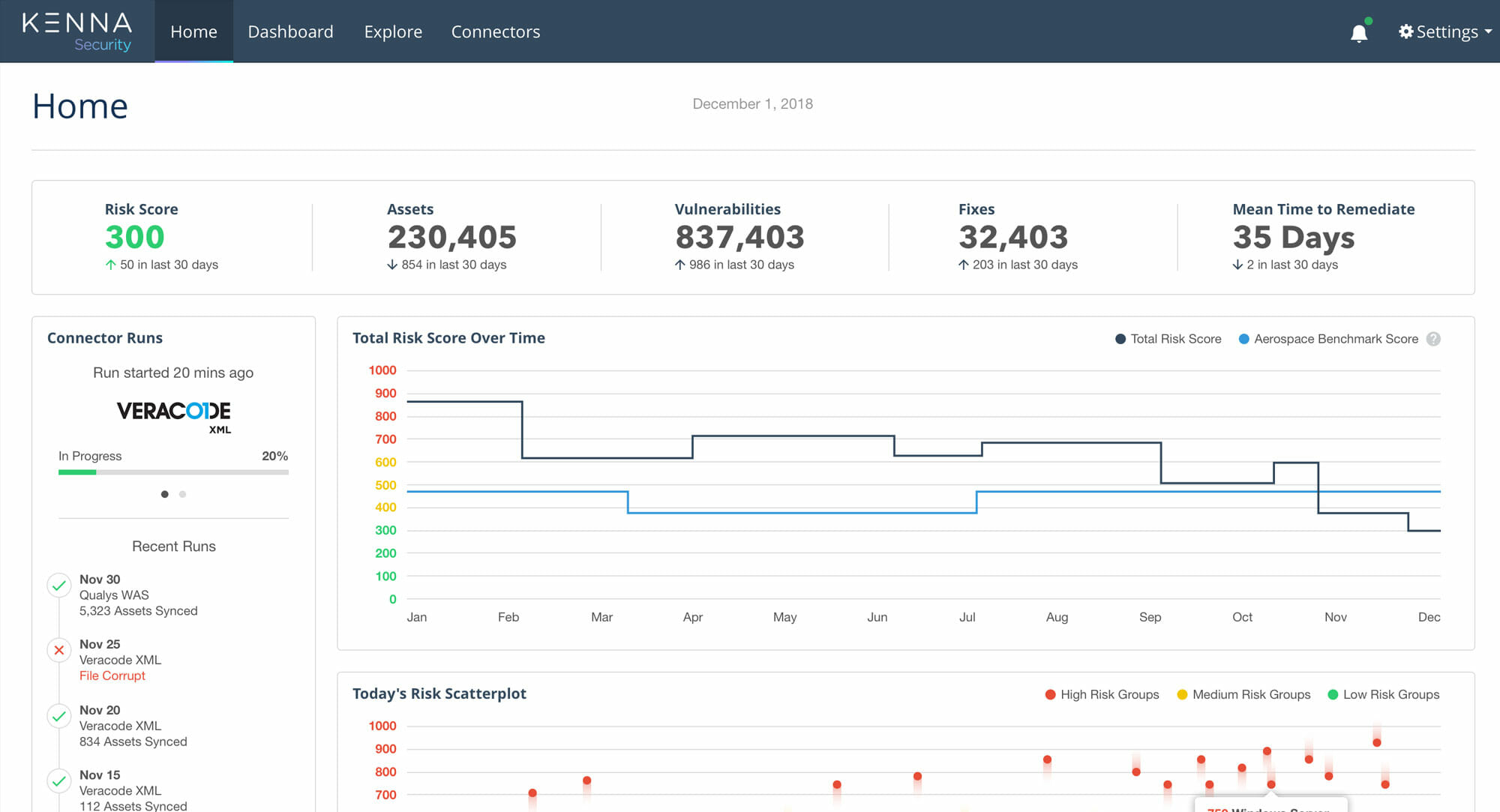
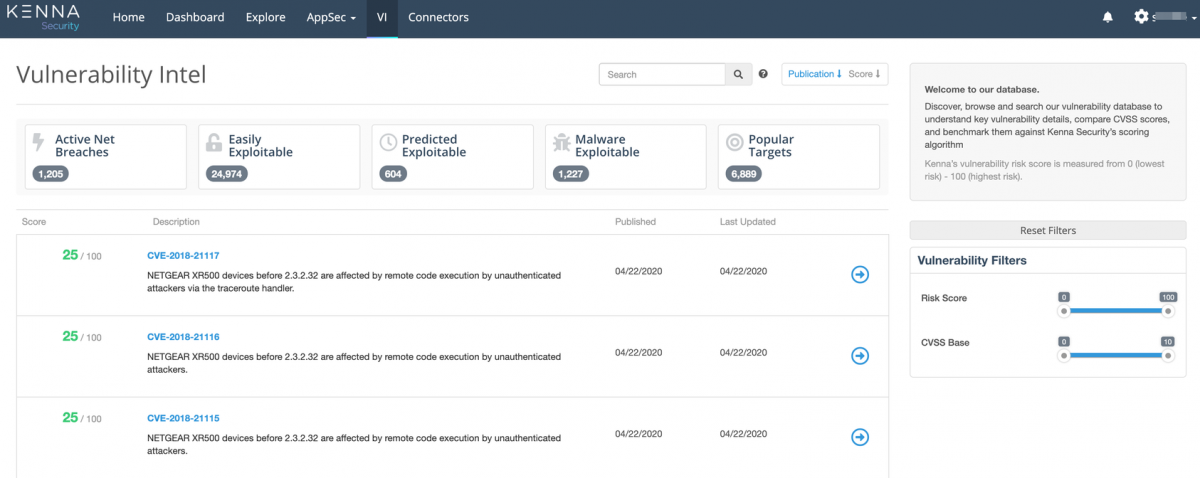
There are three main components of scoring in cisco vulnerability management The changes that we made were to update the logo, text references, and adopt cisco’s color and naming conventions. Understanding these scoring concepts for vulnerabilities, assets and risk meters will help you use cisco vulnerability.
Simplify your security with Kenna
Vulnerability scoring is designed to create a prioritized order of remediation The kenna help center has undergone an update to reflect the new cisco vulnerability management brand Unlike the common vulnerability scoring system (cvss) and other static scoring methods, cisco vulnerability managemen.
Searching & filtering guides cisco vulnerability management basics security tool/vulnerability scanner connectors connectors assets / dashboards / risk meters webinars training videos
Using the vulnerability management dashboard page allows you to group your risk meters into views specific to your audience or needs This topic will help you navigate the dashboard page and outlin. The cisco vulnerability management rest api expands what is possible with the cisco vulnerability management platform Using the api allows your team to customize and extend how you use cisco vulne.
Managed in the cloud and powered by nessus technology, tenable.io provid. Once you have access to cisco vulnerability management, you can start exploring and learning about the platform Check out the attached pdf below for the complete getting started guide Use this command to troubleshoot issues by reviewing the check summary.