Kenna Sweets Nude Full Library Vids & Pics Direct Link
Begin Immediately kenna sweets nude signature digital media. Subscription-free on our content hub. Dive in in a boundless collection of media made available in unmatched quality, essential for passionate watching admirers. With just-released media, you’ll always keep current. Seek out kenna sweets nude arranged streaming in retina quality for a truly captivating experience. Access our content portal today to peruse exclusive premium content with free of charge, no credit card needed. Benefit from continuous additions and experience a plethora of original artist media perfect for superior media fans. Act now to see original media—save it to your device instantly! Explore the pinnacle of kenna sweets nude visionary original content with stunning clarity and special choices.
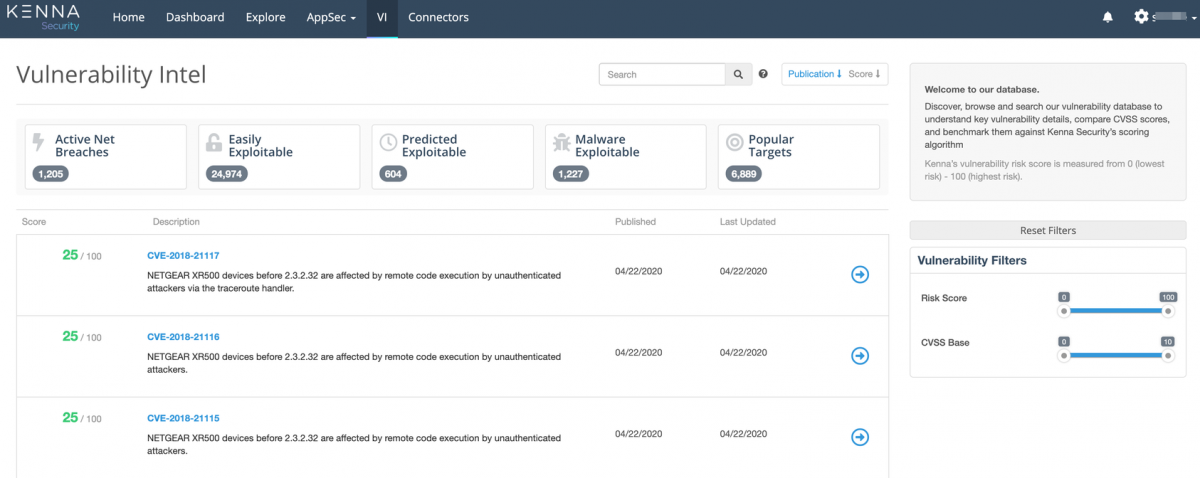
There are three main components of scoring in cisco vulnerability management Before you configure your data importer connector, you have to first create a data importer json formatted file. Understanding these scoring concepts for vulnerabilities, assets and risk meters will help you use cisco vulnerability.
Kenna Kane Biography/Wiki, Age, Height, Career, Photos & More
Vulnerability scoring is designed to create a prioritized order of remediation It is a collection of assets and their vulnerabilities/findings, as well as vulnerability definitions for those vulnerabilities/findings Unlike the common vulnerability scoring system (cvss) and other static scoring methods, cisco vulnerability managemen.
Searching & filtering guides cisco vulnerability management basics security tool/vulnerability scanner connectors connectors assets / dashboards / risk meters webinars training videos
The cisco vulnerability management rest api expands what is possible with the cisco vulnerability management platform Using the api allows your team to customize and extend how you use cisco vulne. Using the vulnerability management dashboard page allows you to group your risk meters into views specific to your audience or needs This topic will help you navigate the dashboard page and outlin.
Once you have access to cisco vulnerability management, you can start exploring and learning about the platform Check out the attached pdf below for the complete getting started guide Managed in the cloud and powered by nessus technology, tenable.io provid. Use this command to troubleshoot issues by reviewing the check summary.

The data importer is a connector that ingests a standard json format for bringing vulnerability data into cisco vulnerability management