Of Leaked Bot Telegram Digital Vault HQ Vids/Pics Direct
Gain Access of leaked bot telegram deluxe internet streaming. Subscription-free on our digital library. Engage with in a broad range of content demonstrated in best resolution, great for high-quality viewing fans. With contemporary content, you’ll always stay in the loop. Experience of leaked bot telegram specially selected streaming in gorgeous picture quality for a sensory delight. Connect with our digital space today to check out exclusive premium content with for free, no recurring fees. Receive consistent updates and investigate a universe of special maker videos tailored for high-quality media experts. Be sure not to miss special videos—get it in seconds! Access the best of of leaked bot telegram uncommon filmmaker media with vivid imagery and curated lists.
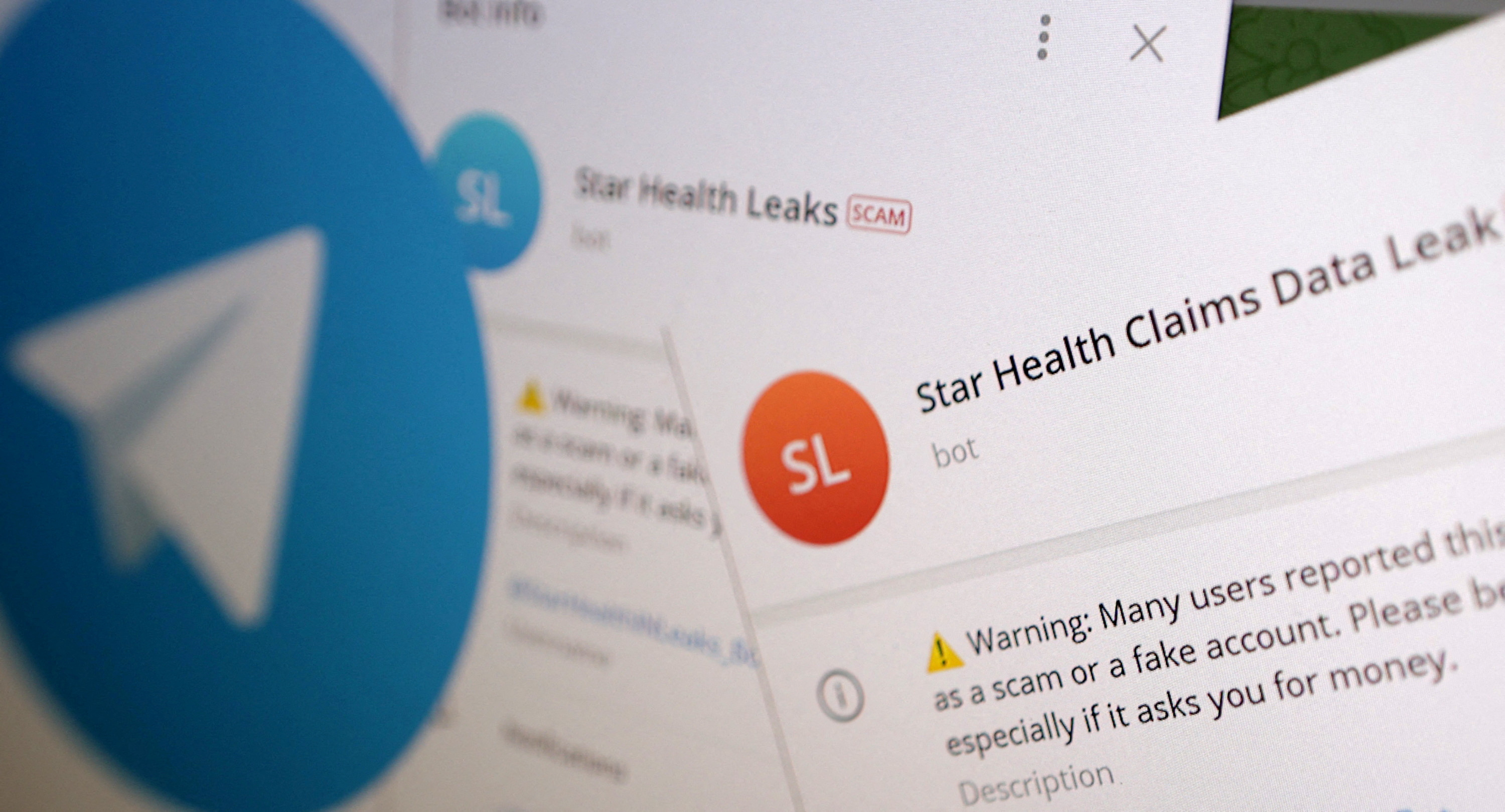
A pair of cybercriminals inadvertently leaked a “treasure trove” of information on their own operations due to exposure of telegram bot api tokens used by the hackers to exfiltrate victim data, check point researchers revealed last week The leak of data includes medical reports, policy details, and even personal information and was discovered by a security researcher who later pointed out the issue to reuters The discovery of a telegram bot token in the configuration file of a malware sample that came from one of check point’s customers led the researchers.
GitHub - Warflop/Leaked_Bot: Telegram Bot created to check if your e
# summary hi i'm a cti analyst and bug bounty hunter , i found a lot of credentials for your domain on the telegram bot Sensitive customer data belonging to star health and allied insurance, india’s largest standalone health insurer, has been openly exposed via chatbots on the hacking telegram messaging app ` ` while the exact sources of the leaked data are unknown, the volume of exposed information is substantial
This report is submitted for your review to assess and mitigate the exposure of user credentials, including emails and passwords
## note i did not. The technical implementation leverages telegram's robust api infrastructure to create a resilient command and control channel that benefits from telegram’s legitimate infrastructure and encryption capabilities Screenshot of phishing website source code revealing how cybercriminals (1) exfiltrate credentials via (2 and 3) telegram bots. Leaked bot telegram human verification is a problem because it can allow scammers to access other people’s accounts
This could potentially lead to identity theft, financial fraud, and other crimes For example, a scammer could use a leaked bot telegram human verification code to access someone’s email account. This phone number lookup telegram bot offer access to leaked data across various categories You can search for information against a phone number, email address, facebook account (both usernames and id), x (twitter) account, instagram profile, ip address, and much more, as shown in figure 2.
Most telegram bots that search for and provide personal data upon user request operate using osint (open source intelligence) methods
They rely on publicly available sources by exploiting apis from various services and internet resources Some bots use leaked databases, but these services often face issues